Our protected mobile services are more than just a simple smartphone. It is a complete solution that provides e highest level of security for your communication.
We have carefully designed and implemented every component of our services, hardware, software and support, to ensure that your data and conversations are safe from any threats.
You use our solution.
We take care that all your needs are met.
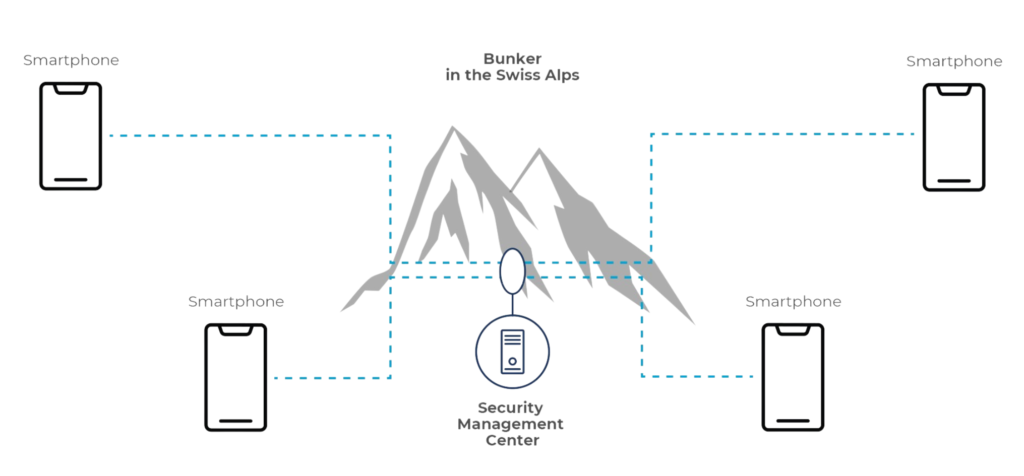
The Security Management Center (SMC) is located in a bunker in the Swiss Alps, ensuring the highest level of safety and privacy. The SMC manages and updates all security and network parameters. This includes user account management, address book management, license management and security key generation and distribution.
Protected hardened smartphones with VPN connection, allowing you to securely access your corporate network from anywhere in the world. The hardened smartphone is purchased exclusively from Swiss Protected Mobile Services. This service is rented from us annually.
The strong symmetric military encryption AES 256, ensures that your voice- and video calls, chat and file
transfers are encrypted and protected from unauthorized access.
Integrated address directory, allowing you to easily find and contact your team members. The address book is managed securely in the SMC in the bunker.
Various security elements have been implemented in the solution, giving you full control over your device and data.
The management system (SMC) for our Swiss Protected Mobile Services is located in a bunker in the Swiss Alps and offers several advantages:
The bunker is protected from external influences such as natural disasters, vandalism or unauthorized access.The bunker’s infrastructure has redundant data lines and power supplies, which ensure high availability of the system.All these measures guarantee high physical security and reliability of our management system.The bunker’s infrastructure uses cold mountain water to efficiently cool IT-System devices and server farms. The server rooms are ventilated with low oxygenated air. In addition, the entire bunker is equipped with modern CO2 extinguishing systems, which can fight a fire quickly and effectively.
Our protected communication network is designed for professionals who need to communicate in sensitive and confidential situations. Whether you are a government official, a business executive, a journalist or a human rights activist, our product will provide you with the best communication solution.
We appreciate your interest in our services. If you need any assistance or clarification, please feel free to reach out to us. Our team is always ready to support you.
Internet access is required for the services. This can be any WIFI access or a Telecom provider data card in the smartphone. If you use a public WIFI connection, your calls are free of charge worldwide.
The communication between the smartphones is end-to-end encrypted. Furthermore, it is not routed through the management system in the bunker. No intermediate server. You are completely protected.
For top secret means that you are completely protected. You get a specially hardened smartphone that does not allow any kind of installations. This means that you cannot install applications, even from APP stores. As a result, malware cannot install itself or be installed.
For confidential use the transfer of communication and data is completely secured as it is with the top secret version. However, you can install APPs but this means that you are responsible for the security of your smartphone. The advantage of this solution is that you can use your own Smartphone and your familiar application environment.
For confidential use the transport of the messages is completely secured as with the version top secret. However, you can install APPs but this means that you are responsible for the security of your smartphone. The advantage is that you can use your familiar APP environment.
The management system is the key element of our solution and must be protected in particular against:
When you start the hardened smartphone, our proprietary operating system is loaded. It does not allow any more to install applications or programs that are not approved by us. Therefore, it is also not possible for malicious software to install itself or be installed.
Malware cannot install itself or be installed because our proprietary OS in the hardened smartphone does not allow it.
Software updates are delivered directly from the security management system in the bunker and are installed automatically on the user devices.
No malware or other unauthorized programs can be installed on the hardened smartphone. On clients demand we can install a verified Internet browser and an email client. The Internet traffic will be verified and controlled in the Security Management IT-environment. Emails and the Internet cannot cause security damage to the hardened smartphone.
These services come with an extra cost.
A service of
Copyright © 2023 Graphodata SAGL